Hello,
A Cross-Site Scripting (XSS) vulnerability was reported on your website:
https://www.xssposed.org/incidents/78581/
Current vulnerability status is “unpatched”. It is recommended to fix the vulnerability rapidly to prevent its malicious exploitation by hackers.
Later you can request to check that the vulnerability was patched in order to change vulnerability status.
Best regards,
XSSposed.org Team
IMPORTANT: This is an automated notification that is sent only once. If in the future you wish to receive notification about all upcoming vulnerabilities on helloacm.com subscribe online for free: www.xssposed.org/email-alerts/

xss-attack
screen-78581
Vulnerable URL:
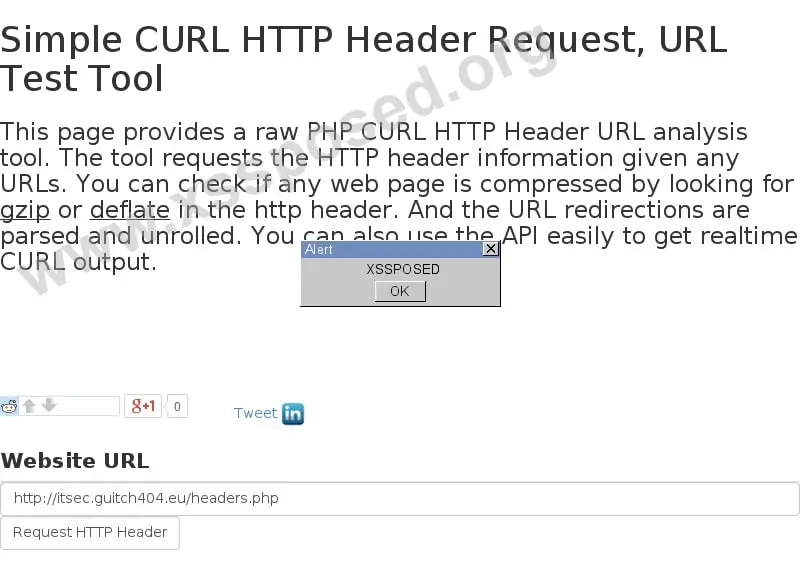
https://helloacm.com/curl/?url=http://itsec.guitch404.eu/headers.php
Vulnerability Details:
Verified Yes, at 13/08/2015 Latest check for patch 13/08/2015 15:24 GMT Type XSS Alexa Rank 220715
Patched Yes, at 13/08/2015
Why?
The special HTML tag characters < and > are not escaped so that the malicious code can be prepared in the output string. When this full URL is given to user, the code may be executed in user’s browsers.
The API pure output explains itself: https://helloacm.com/api/curl/?url=http://itsec.guitch404.eu/headers.php
returns:
"HTTP\/1.1 200 OK\r\nSet-Cookie: 300gpBAK=R4178785959; path=\/; expires=Tue, 18-Aug-2015 23:47:47 GMT\r\nContent-Type: text\/html; charset=UTF-8\r\nSet-Cookie: 300gp=R394784785; path=\/; expires=Tue, 18-Aug-2015 23:46:23 GMT\r\nServer: Apache\r\nItSec: <script>alert(\"XSSPOSED\")<\/script>\r\nAccess-Control-Allow-Origin: *\r\nVary: Accept-Encoding\r\nContent-Encoding: gzip\r\nDate: Tue, 18 Aug 2015 22:32:37 GMT\r\nConnection: keep-alive\r\nX-Geo: varn32.rbx5\r\nX-Geo-Port: 1011\r\nX-Cacheable: Not cacheable: no cache headers from backend\r\n\r\n"
Patch Solution
Add a filter to the output display using htmlspecialchars function in PHP that will translate any special characters such as < to <
–EOF (The Ultimate Computing & Technology Blog) —
loading...
Last Post: Firmware Upgrade for TL-WR740N Router
Next Post: Refactoring Re-sampling Algorithm using O(n) Hashtable
Hi,
I found another vulnerability. How can I contact you?
Guitch404
dr.zhihua.lai [AT] gmail.com