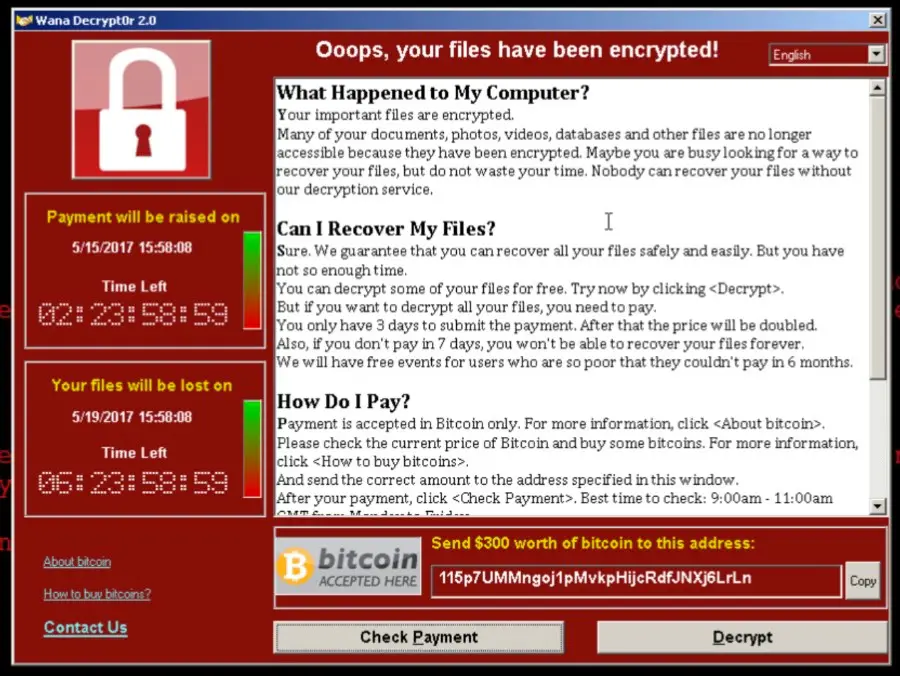
As widely reported, hackers launched a global ransomware campaign last Friday, May 12, known as “WannaCry Ransomware“. Targeting tens of thousands of companies and governmental organizations, this campaign encrypted files on infected computers and asked computer administrators to pay a ransom in order to regain access.
This particular ransomware exploited a vulnerability that allows remote code execution via the Microsoft Server Message Block (SMBv1) server. Microsoft has released a security update that addresses this vulnerability, and QuickHostUK has been working diligently to make sure all internal systems have had this vulnerability addressed. We have not yet identified nor do we currently expect any interruption to our production environments.
QuickHostUK managed service customers likely already have this patch applied, as it was released in March, two patching cycles ago. Clients who opted out of the QuickHostUK patch management process should review their environments and apply the necessary patches immediately to minimize exposure.
QuickHostUK is working with our managed service customers to help ensure they have the patch applied and – where they have not – we are either applying it manually or scheduling times to apply it.
For clients looking to protect themselves, we offer the recommendations outlined below.
Protection Recommendations to WannaCry Ransomware Attacks
- Install Microsoft security patchesthat eliminate the vulnerability exploited by WannaCry.
- These patches were issued for newer versions of Windows in March.
- Microsoft has also taken the unprecedented step of issuing a patch for Windows XP, an old operating system that Microsoft no longer supports on a regular basis but is doing so in this critical situation.
- Engage your IT security team to back up critical data, so that even if data is locked up, there are copies elsewhere, to which a company can turn.
- If they have not done so already, IT security teams should deploy antivirus and malware signatures associated with the threat. The Department of Homeland Security’s cyber operations center has posted these signatures.
- If they have not done so already, clients should formulate a ransomware incident response plan, so their company is ready to spring into action if its systems are hit.
These plans should consider whether or not to pay ransom; whether and how to interact with law enforcement and regulators; a process to restore operations; and public and customer communication actions. - Consider requiring all employees with email access to refresh themselves on counter-phishing training. Over the weekend, a security researcher identified a “kill switch” that partially stopped WannaCry’s spread.
However, the hackers may reconfigure their assault around this kill switch, with new phishing emails to come in the days ahead.
–EOF (The Ultimate Computing & Technology Blog) —
loading...
Last Post: How to Reduce the Risk of WannaCry Ransomware/Virus?
Next Post: How to Evaluate Stochastic Algorithms?